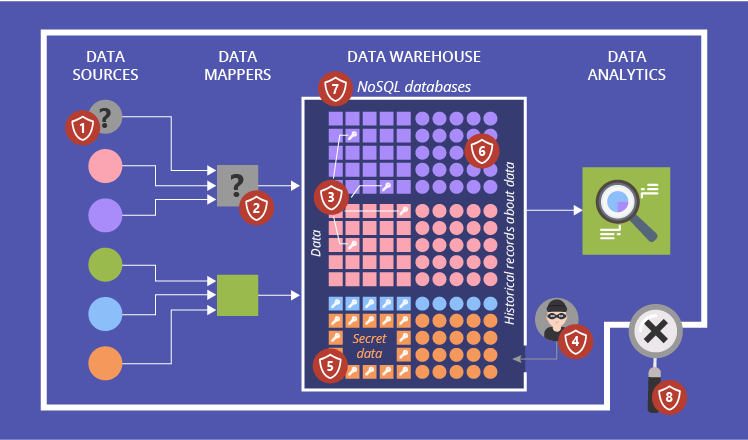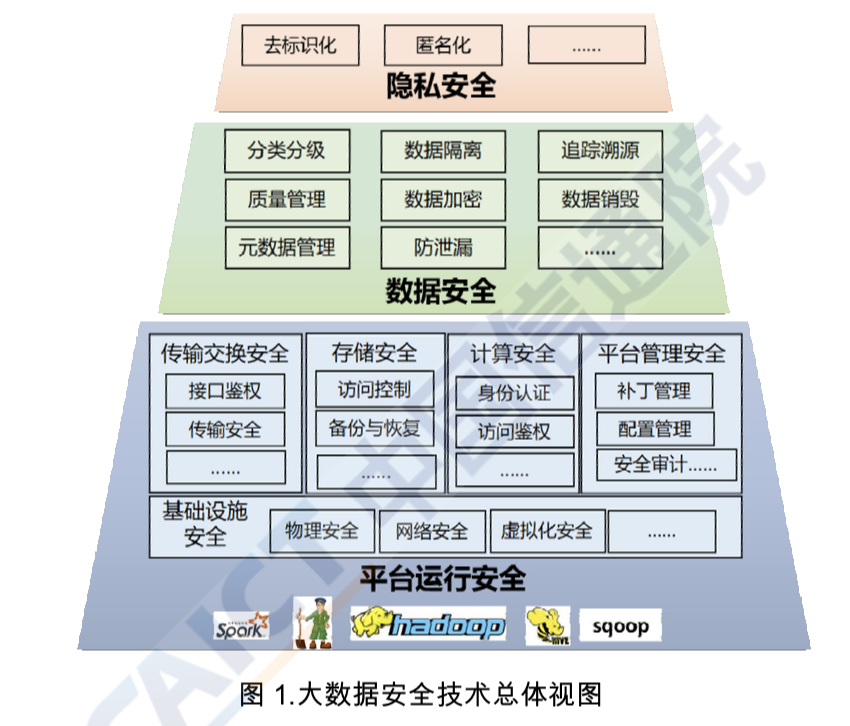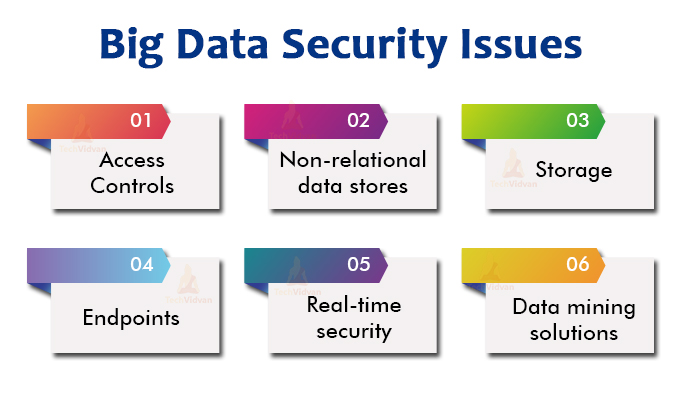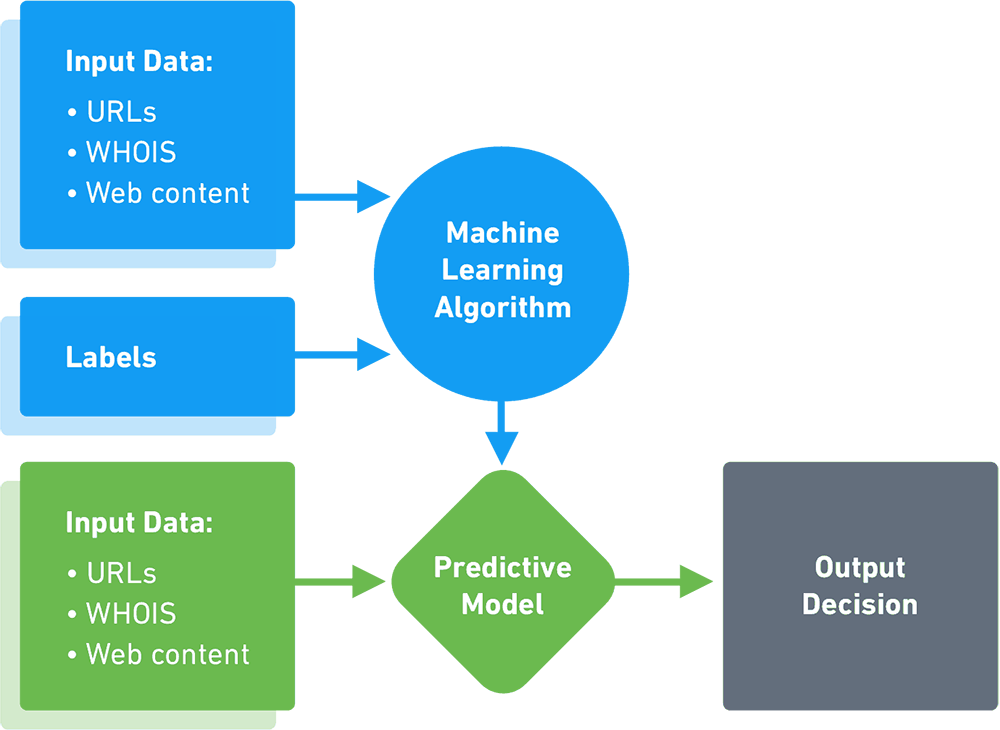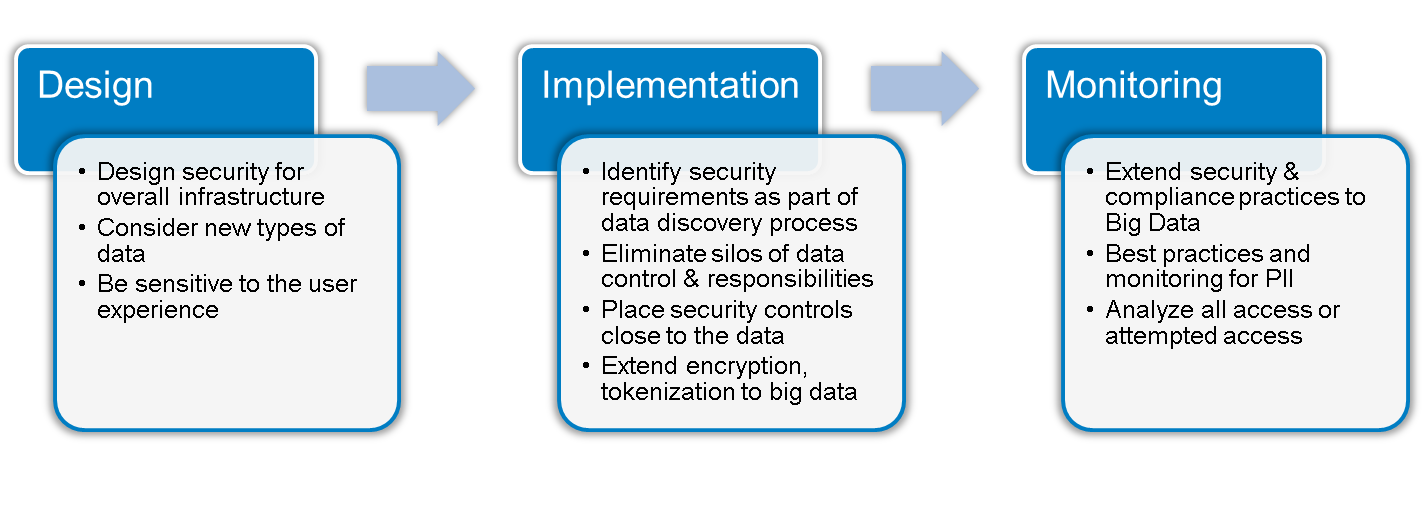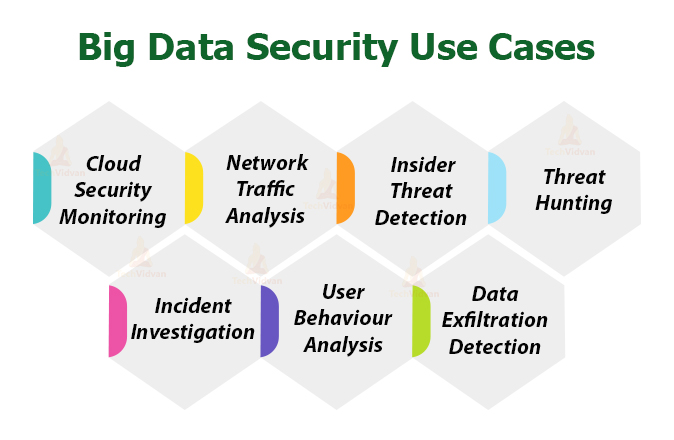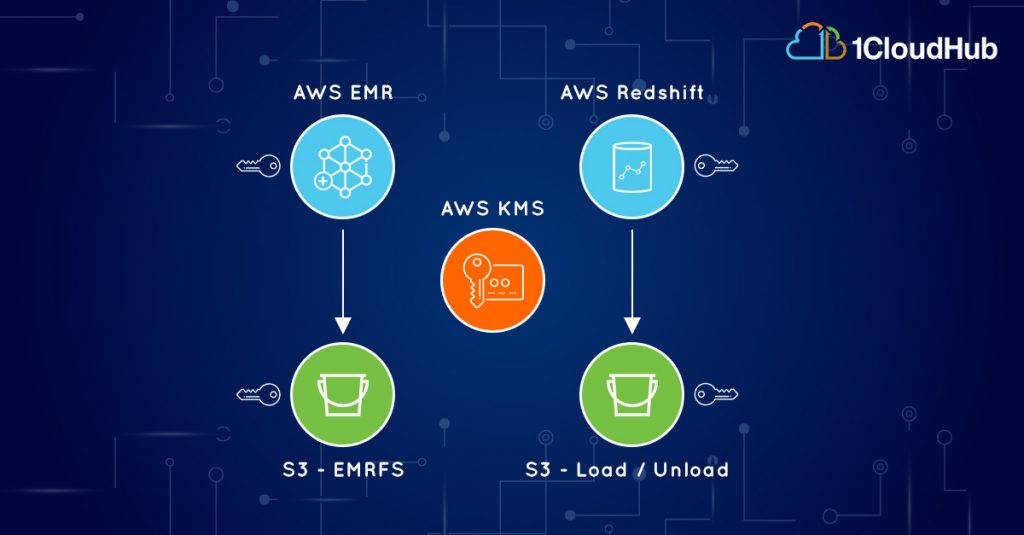
Data security management with AWS Big Data PaaS - 1CloudHub: Cloud engineers and transformation enablers across multiple clouds.
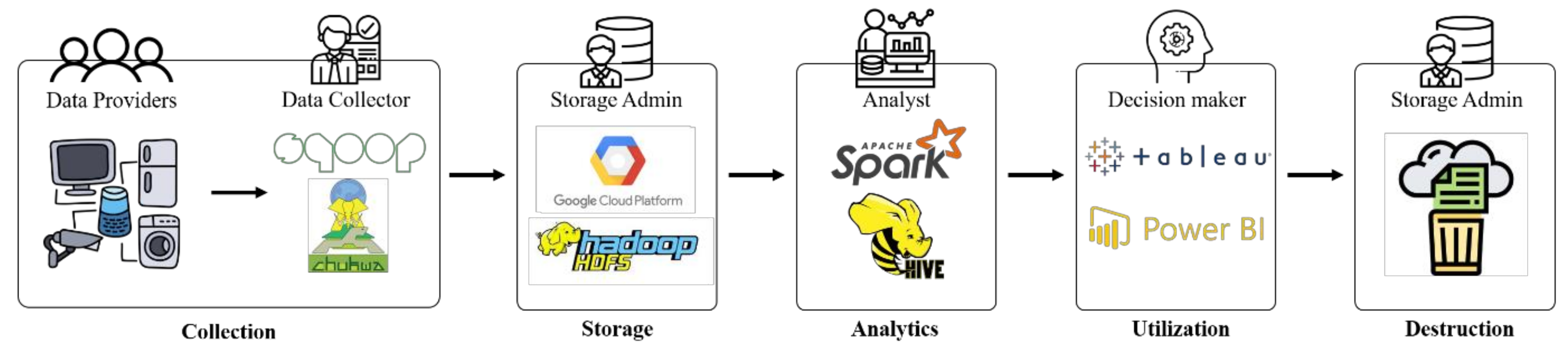
Sustainability | Free Full-Text | Security and Privacy in Big Data Life Cycle: A Survey and Open Challenges

Security Analytics and Cybersecurity: Big Data is Pivotal in Predicting Future Threats | Micro Focus Community

The Challenges and Opportunities of Big Data in Cybersecurity | Data Center Knowledge | News and analysis for the data center industry
Big Data Security Solutions, Analytics and Management | by Xenonstack | XenonStack Security | Medium

1-Challenges in Big Data security How Can Big Data Security be improved? | Download Scientific Diagram