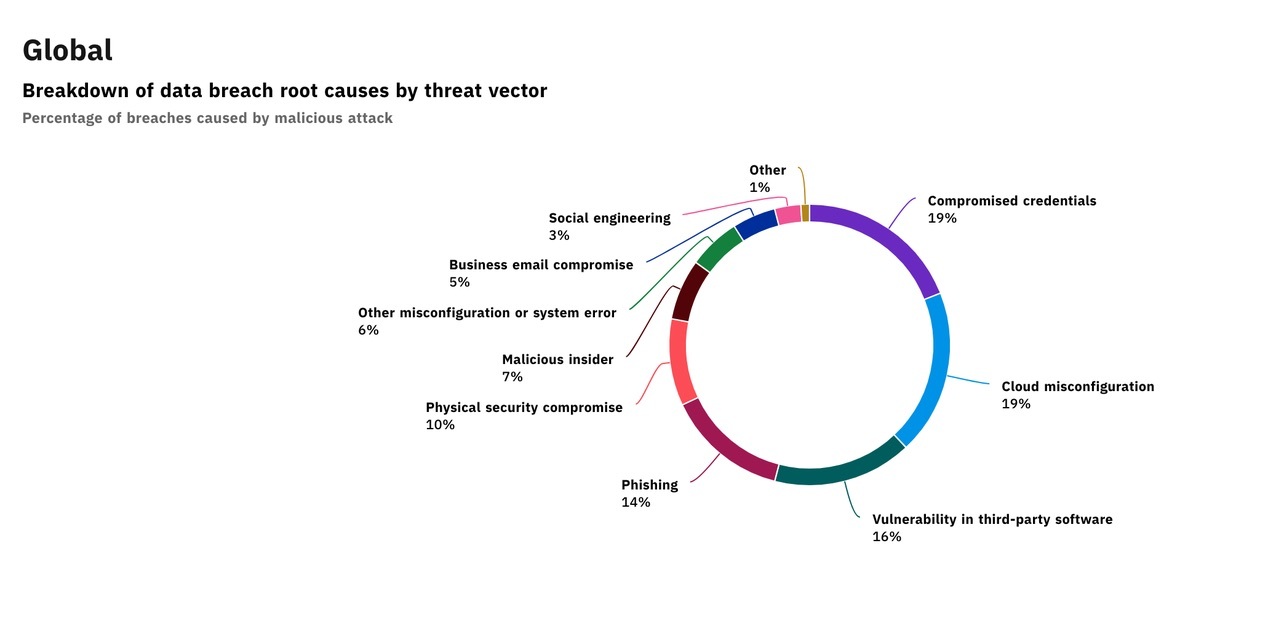
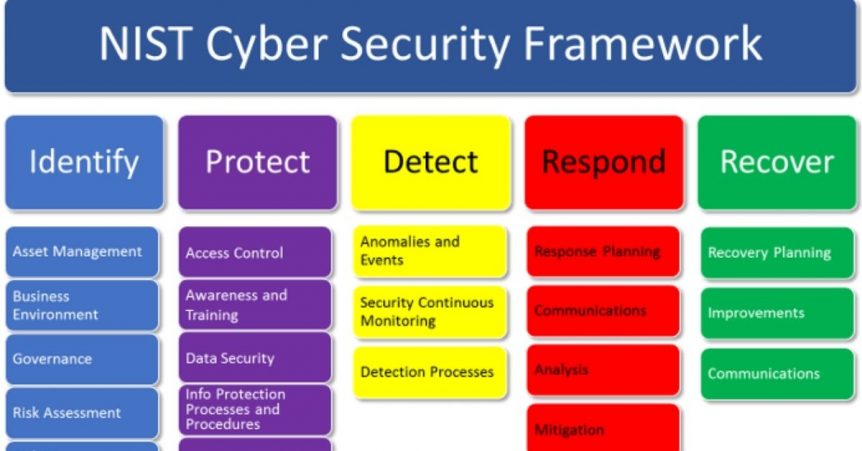
9 Important Elements to Corporate Data Security Policies that Protect Data Privacy | 2016-05-10 | Security Magazine
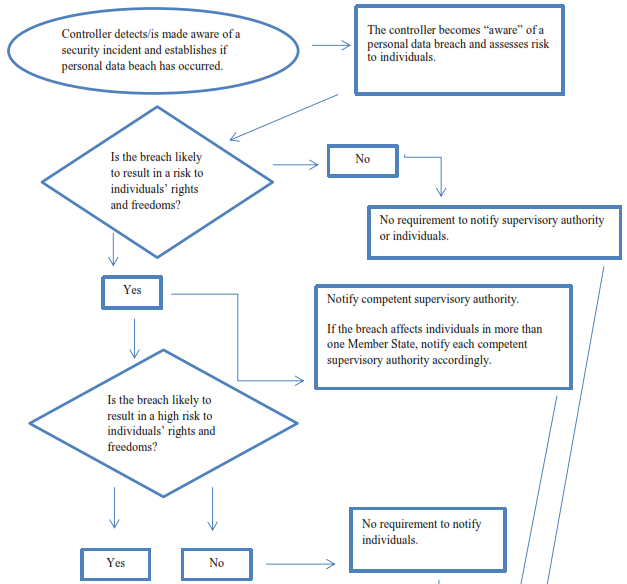
Page Compare: Guidelines on Personal data breach notification under Regulation 2016/679 - Adopted on 3 October 2017 (as last Revised and Adopted on 6 February 2018) (WP250rev.01) | Better Regulation

mHealth Data Security, Privacy, and Confidentiality: Guidelines for Program Implementers and Policymakers — MEASURE Evaluation
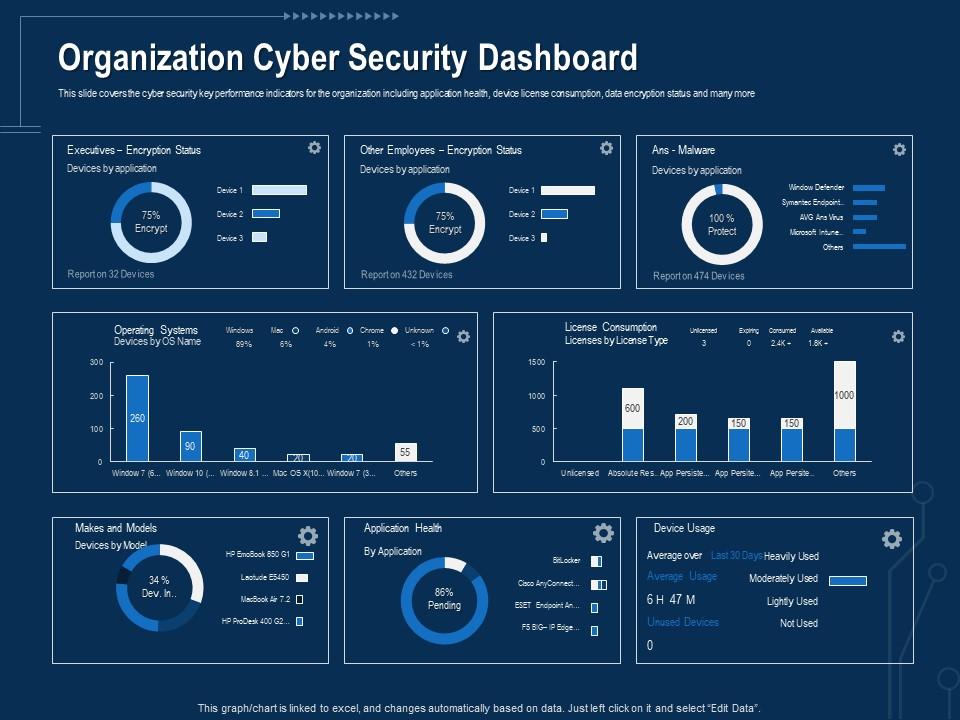

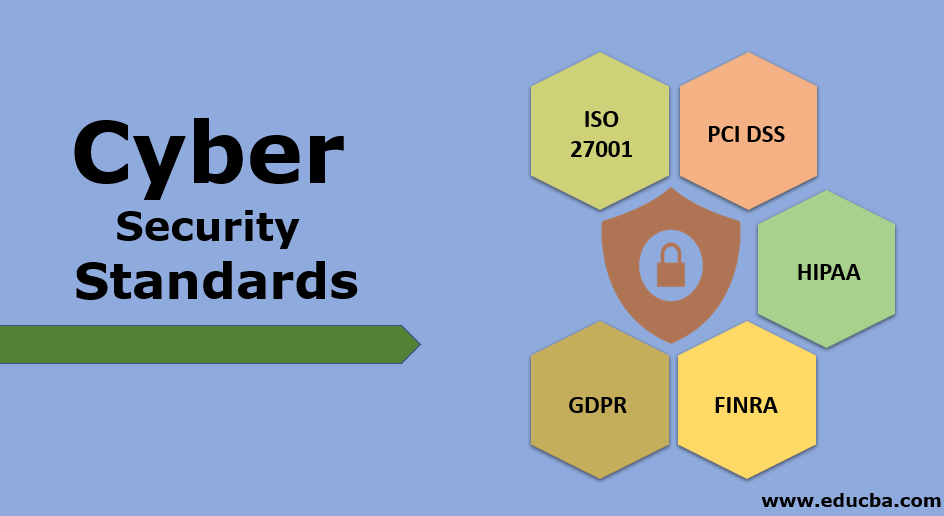
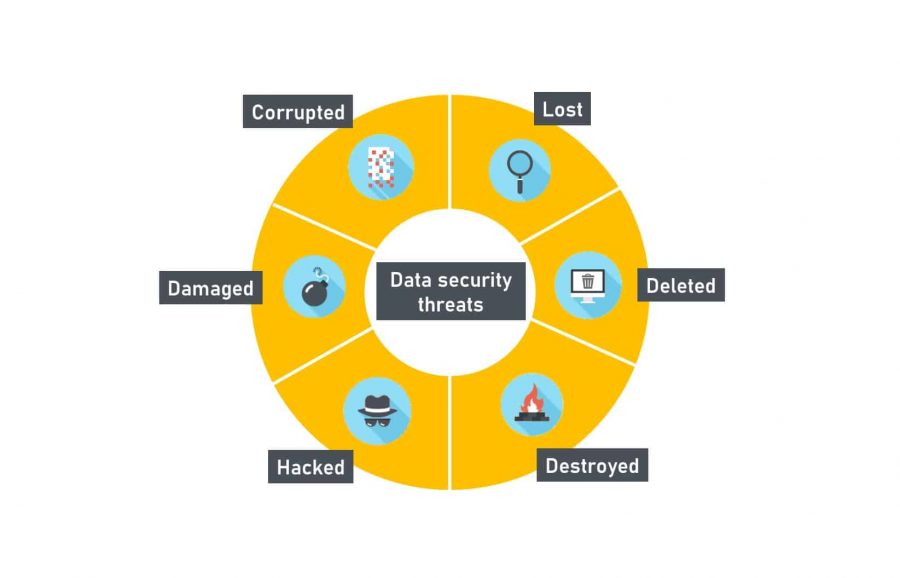
![22 Best Practices for Protecting Data Privacy in 2022 [Infographic] - TitanFile 22 Best Practices for Protecting Data Privacy in 2022 [Infographic] - TitanFile](https://www.titanfile.com/wp-content/uploads/2022/03/Protecting-Data-Privacy-in-2022-Infographic-2.png)
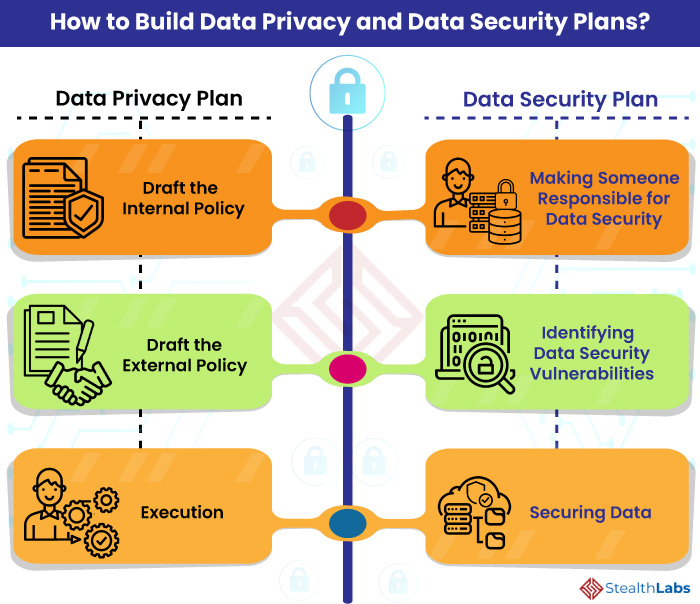




![Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager Data Privacy vs. Data Security [definitions and comparisons] – Data Privacy Manager](https://dataprivacymanager.net/wp-content/uploads/2020/08/visual-representation-of-data-privacy-and-data-security-areas.png)