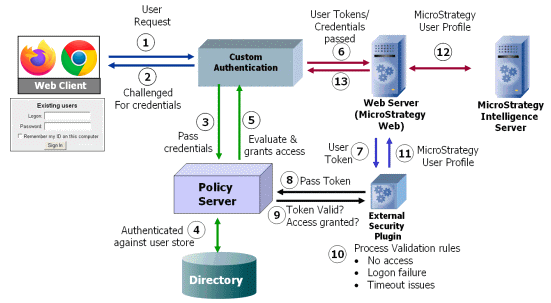
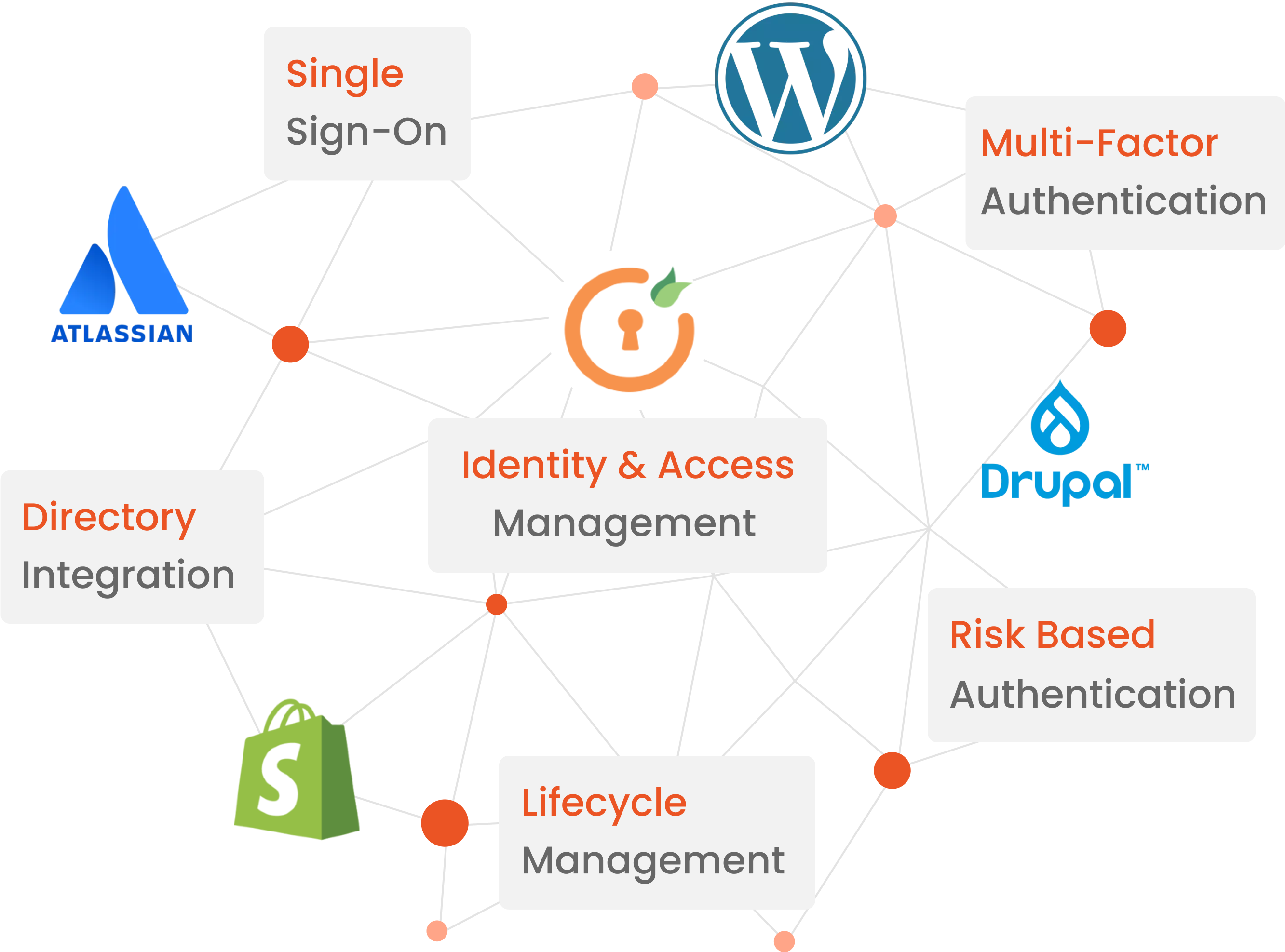
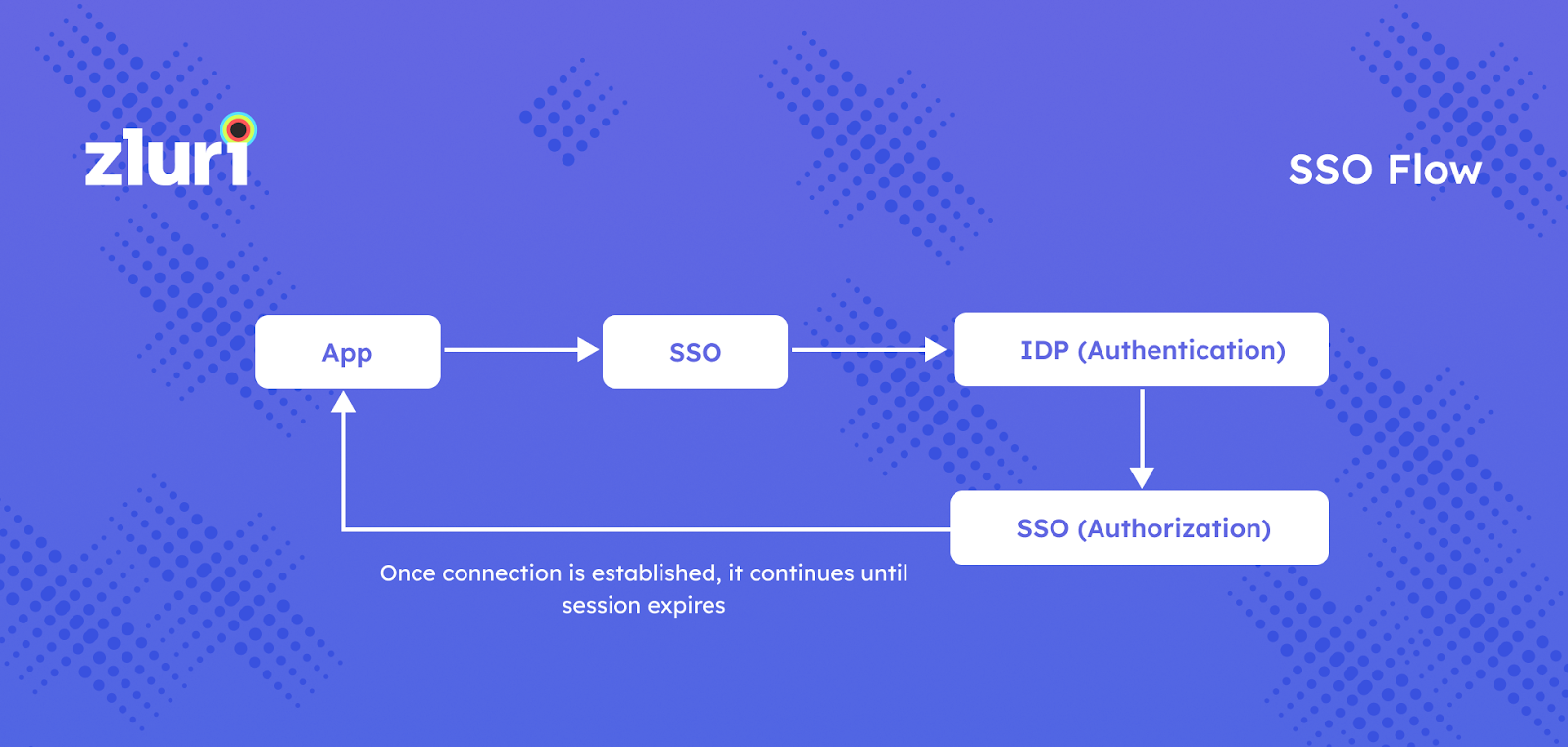
![PDF] Single Sign-On : Risks and Opportunities of Using SSO (Single Sign-On) in a Complex System Environment with Focus on Overall Security Aspects | Semantic Scholar PDF] Single Sign-On : Risks and Opportunities of Using SSO (Single Sign-On) in a Complex System Environment with Focus on Overall Security Aspects | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/df3f226a4d107c670b2c7692aef4cb7fd4f753dc/10-Figure1.1-1.png)
PDF] Single Sign-On : Risks and Opportunities of Using SSO (Single Sign-On) in a Complex System Environment with Focus on Overall Security Aspects | Semantic Scholar

Vulnerabilities in Single Sign-On services could be abused to bypass authentication controls | The Daily Swig
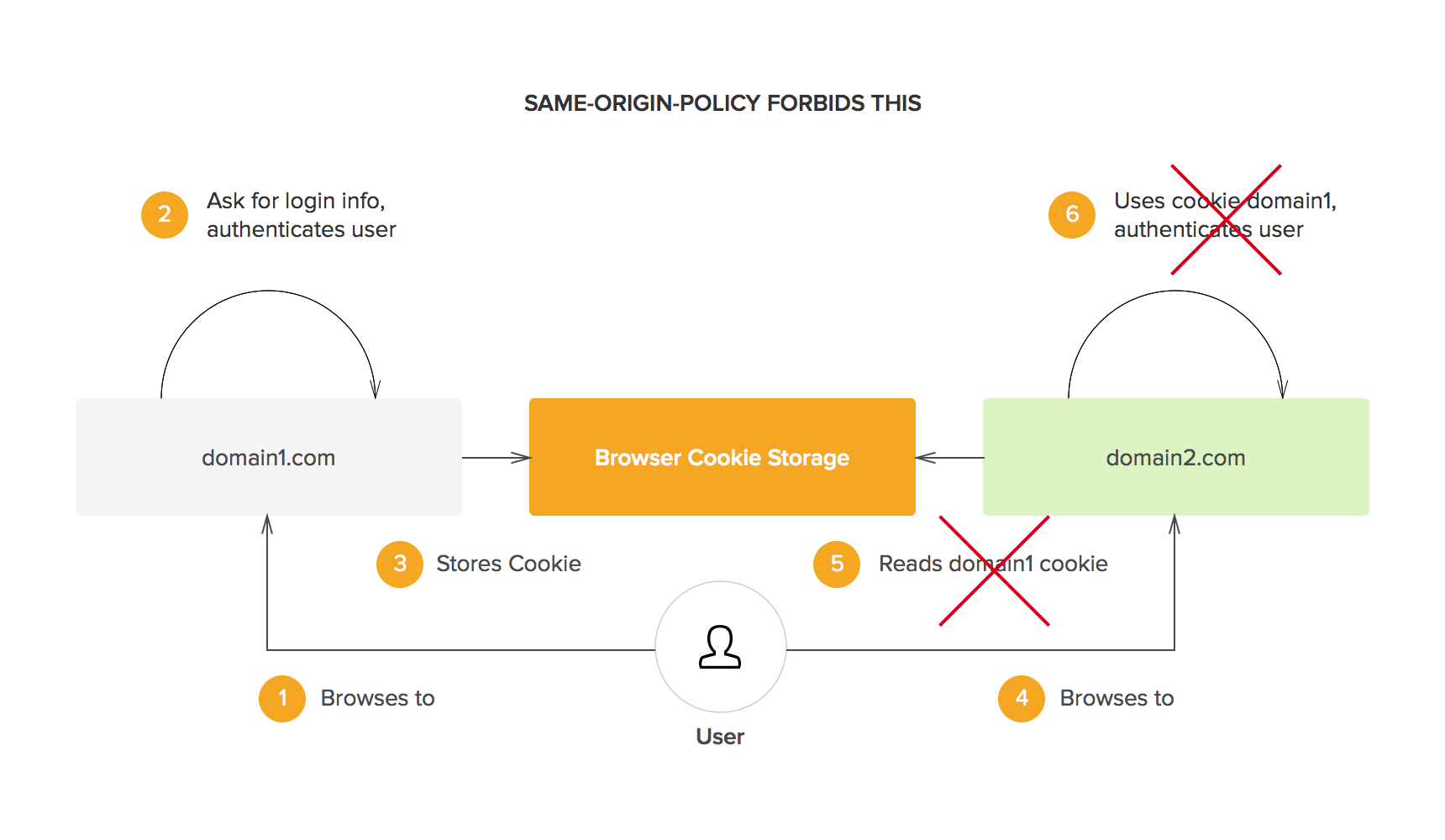
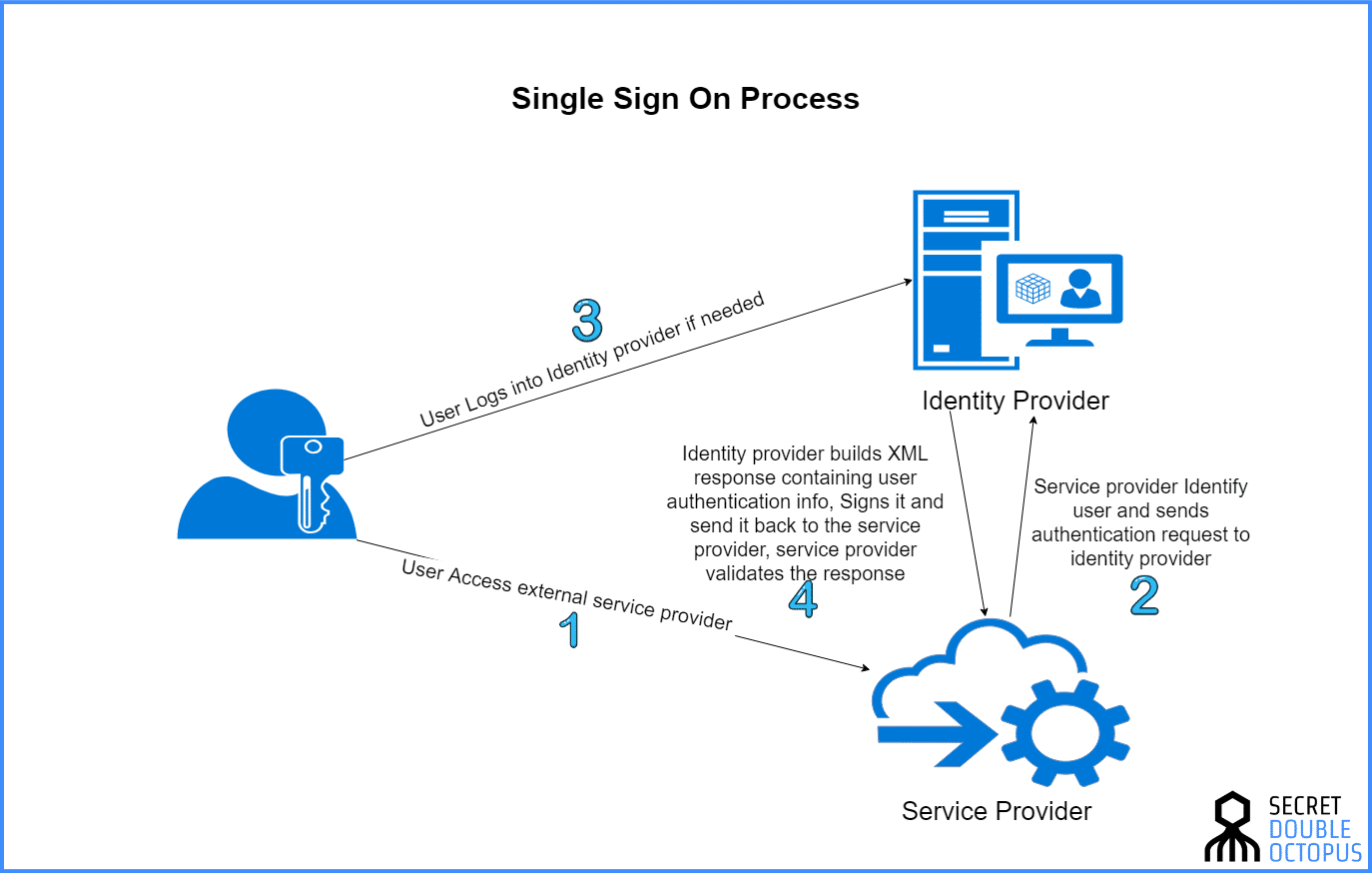
![PDF] Single Sign-On : Risks and Opportunities of Using SSO (Single Sign-On) in a Complex System Environment with Focus on Overall Security Aspects | Semantic Scholar PDF] Single Sign-On : Risks and Opportunities of Using SSO (Single Sign-On) in a Complex System Environment with Focus on Overall Security Aspects | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/df3f226a4d107c670b2c7692aef4cb7fd4f753dc/13-Figure2.1-1.png)

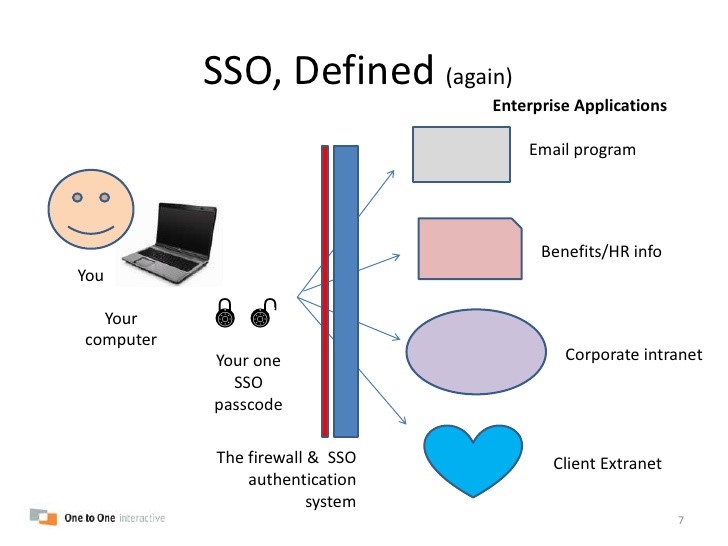
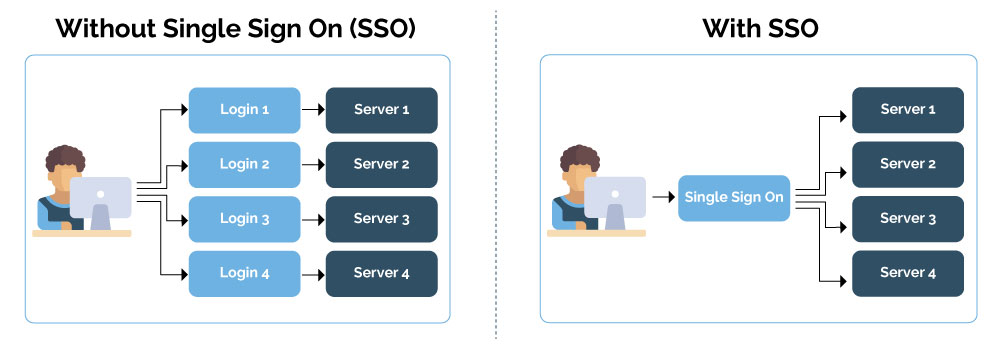
.png)